What is ransomware?
Ransomware is a sophisticated piece of malware that blocks the victim’s access to his/her files.
There are two types of ransomware in circulation:
-
Encrypting ransomware, which incorporates advanced encryption algorithms. It’s designed to block system files and demand payment to provide the victim with the key that can decrypt the blocked content. Examples include CryptoLocker, Locky, CrytpoWall and more.
-
Locker ransomware, which locks the victim out of the operating system, making it impossible to access the desktop and any apps or files. The files are not encrypted in this case, but the attackers still ask for a ransom to unlock the infected computer. Examples include the police-themed ransomware or Winlocker.
Another version pertaining to this type is the Master Boot Record (MBR) ransomware. The MBR is the section of a PC’s hard drive which enables the operating system to boot up. When MBR ransomware strikes, the boot process can’t complete as usual, and prompts a ransom note to be displayed on the screen. Examples include Satana and Petya ransomware.
However, the most widespread type of ransomware is crypto-ransomware or encrypting ransomware, which I’ll focus on in this guide. The cyber security community agrees that this is the most prominent and worrisome cyber threat of the moment.
Ransomware has some key characteristics that set it apart from other malware:
- It features unbreakable encryption, which means that you can’t decrypt the files on your own (there are various decryption tools released by cyber security researchers – more on that later);
- It has the ability to encrypt all kinds of files, from documents to pictures, videos, audio files and other things you may have on your PC;
- It can scramble your file names, so you can’t know which data was affected. This is one of the social engineering tricks used to confuse and coerce victims into paying the ransom;
- It will add a different extension to your files, to sometimes signal a specific type of ransomware strain;
- It will display an image or a message that lets you know your data has been encrypted and that you have to pay a specific sum of money to get it back;
- It requests payment in Bitcoins, because this crypto-currency cannot be tracked by cyber security researchers or law enforcements agencies;
- Usually, the ransom payments has a time-limit, to add another level of psychological constraint to this extortion scheme. Going over the deadline typically means that the ransom will increase, but it can also mean that the data will be destroyed and lost forever.
- It uses a complex set of evasion techniques to go undetected by traditional antivirus (more on this in the “Why ransomware often goes undetected by antivirus” section);
- It often recruits the infected PCs into botnets, so cyber criminals can expand their infrastructure and fuel future attacks;
- It can spread to other PCs connected in a local network, creating further damage;
- It frequently features data exfiltration capabilities, which means that ransomware can extract data from the affected computer (usernames, passwords, email addresses, etc.) and send it to a server controlled by cyber criminals;
- It sometimes includes geographical targeting, meaning the ransom note is translated into the victim’s language, to increase the chances for the ransom to be paid.
The inventory of things that ransomware can do keeps growing every day, with each new security alert broadcasted by our team or other malware researchers.
Encrypting ransomware is a complex and advanced cyber threat which uses all the tricks available because it makes cyber criminals a huge amount of money. We’re talking millions!
Why ransomware creators and distributors target businesses:
- Because that’s where the money is;
- Because attackers know that ransomware can cause major business disruptions, which will increase their chances of getting paid;
- Because computer systems in companies are often complex and prone to vulnerabilities that can be exploited through technical means;
- Because the human factor is still a huge liability which can also be exploited, but through social engineering tactics;
- Because ransomware can affect not only computers, but also servers and cloud-based file-sharing systems, going deep into a business’s core;
- Because cyber criminals know that business would rather not report ransomware attacks for fears of legal or reputation-related consequences;
- Because small businesses are often unprepared to deal with advanced cyber attacks (which ransomware is) and have a lax BYOD (bring your own device) policy.
How do ransomware threats spread?
Ransomware and any other advanced piece of financial or data stealing malware spreads by any available means.
Cyber criminals simply look for the easiest way to infect a system or network and use that backdoor to spread the malicious content.
Nevertheless, these are the most common methods used by cybercriminals to spread ransomware:
- Spam email campaigns that contain malicious links or attachments;
- Security exploits in vulnerable software;
- Internet traffic redirects to malicious websites;
- Legitimate websites that have malicious code injected in their web pages;
- Drive-by downloads;
- Malvertising campaigns;
- SMS messages (which apply to ransomware that targets mobile devices);
- Botnets;
- Self-propagation (spreading from one infected computer to another);
- Affiliate schemes in ransomware-as-a-service (earning a share of the profits by helping further spread ransomware).
Crypto-ransomware attacks employ a subtle mix of technology and psychological manipulation (also known as social engineering).
These attacks get more refined by the day, as cyber criminals learn from their mistakes and tweak their malicious code to be stronger, more intrusive and better suited to avoid cyber security solutions.
That’s why each new ransomware variant is a bit different from its forerunner. Malware creators incorporate new evasion tactics and pack their “product” with piercing exploit kits, pre-coded software vulnerabilities to target and more.
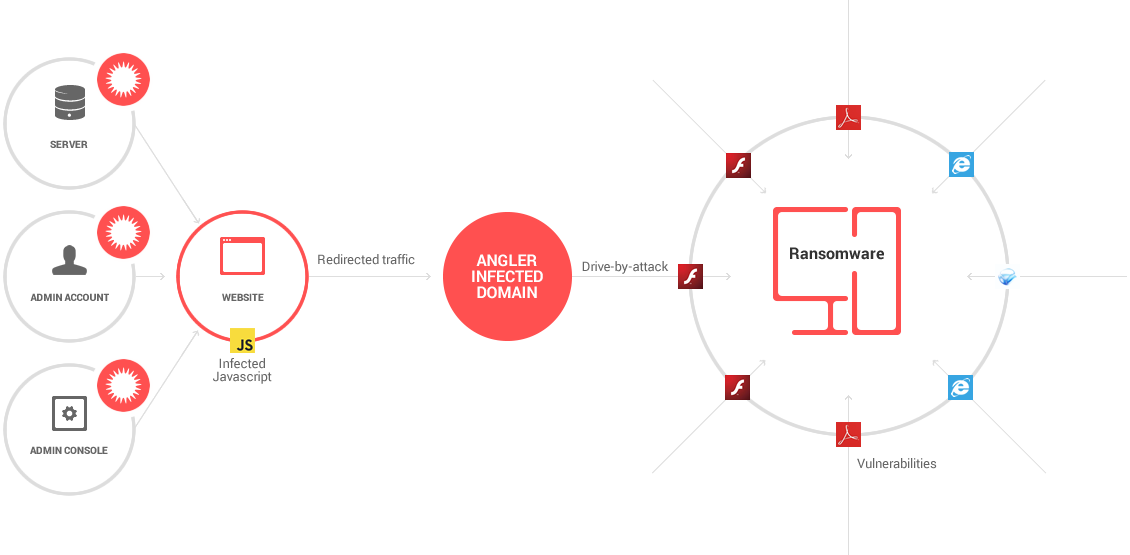
For example, here’s how online criminals find vulnerable websites, inject malicious JavaScript code in them and use this trigger to redirect potential victims to infected websites.
Which gets us to the next important answer in our common quest to understand ransomware attacks.
How do ransomware infections happen?
Though the infection phase is slightly different for each ransomware version, the key stages are the following:
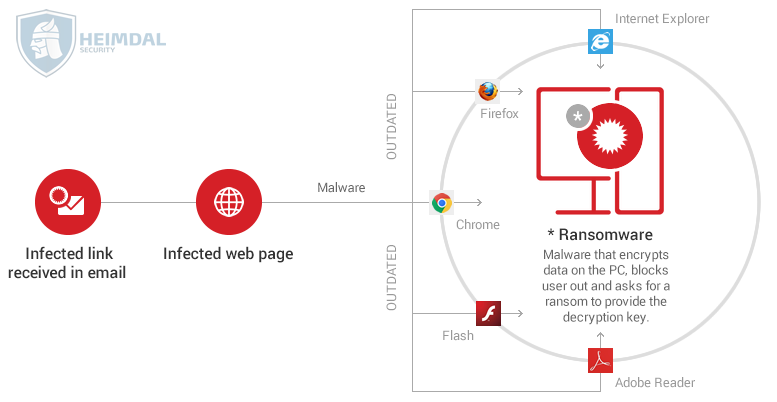
- Initially, the victim receives an email which includes a malicious link or an malware-laden attachment. Alternatively, the infection can originate from a malicious website that delivers a security exploit to create a backdoor on the victim’s PC by using a vulnerable software from the system.
- If the victim clicks on the link or downloads and opens the attachment, a downloader (payload) will be placed on the affected PC.
- The downloader uses a list of domains or C&C servers controlled by cyber criminals to download the ransomware program on the system.
- The contacted C&C server responds by sending back the requested data, in our case, the ransomware.
- The ransomware starts to encrypt the entire hard disk content, personal files and sensitive information. Everything, including data stored in cloud accounts (Google Drive, Dropbox) synced on the PC. It can also encrypt data on other computers connected in the local network.
- A warning pops up on the screen with instructions on how to pay for the decryption key.
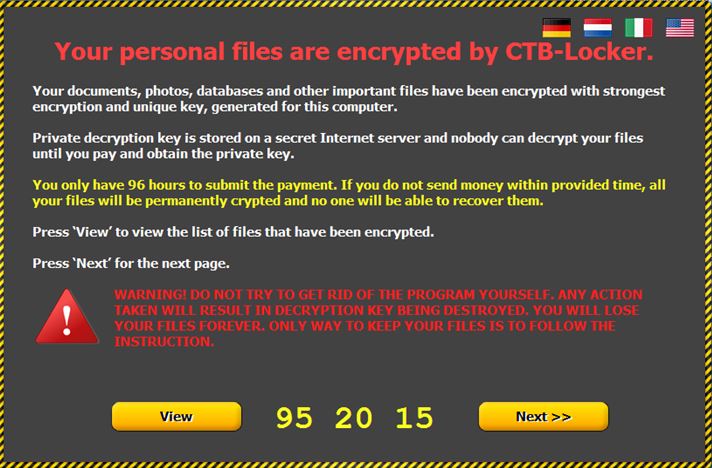
Everything happens in just a few seconds, so victims are completely dumbstruck as they stare at the ransom note in disbelief.
Most of them feel betrayed, because they can’t seem to understand one thing:
But I have antivirus!
Why didn’t it protect me from this?
Why ransomware often goes undetected by antivirus
I’ve mentioned the evasion tactics that ransomware uses more than once. This collection of technical methods ensures that crypto-ransomware infections can stay below the radar and:
- Not get picked up by antivirus products
- Not get discovered by cyber security researchers
- Not get observed by law enforcement agencies and their own malware researchers.
The rationale is simple: the longer a malware infection can persist on a compromised PC, the more data it can extract and the more damage it can do.
So here are just a few of the tactics that ransomware employs to remain covert and maintain the anonymity of its makers and distributors:
- Communication with Command & Control servers is encrypted and difficult to detect in network traffic;
- It features built-in traffic anonymizers, like TOR and Bitcoin, to avoid tracking by law enforcement agencies and to receive ransom payments;
- It uses anti-sandboxing mechanisms so that antivirus won’t pick it up;
- It employs domain shadowing to conceal exploits and hide the communication between the downloader (payload) and the servers controlled by cyber criminals (where the ransomware is stored);
- It features Fast Flux, another technique used to keep the source of the infection anonymous;
- It deploys encrypted payloads which can make it more difficult for antivirus to see that they include malware, so the infection has more time to unfold;
- It has polymorphic behavior that endows the ransomware with the ability to mutate enough to create a new variant, but not so much as to alter the malware’s function;
- It has the ability to remain dormant – the ransomware can remain inactive on the system until the computer it at its most vulnerable moment and take advantage of that to strike fast and effectively.
If you’re keen on reading more about Ransomware and other potential Cyber Threat, here: https://heimdalsecurity.com/blog/what-is-ransomware-protection